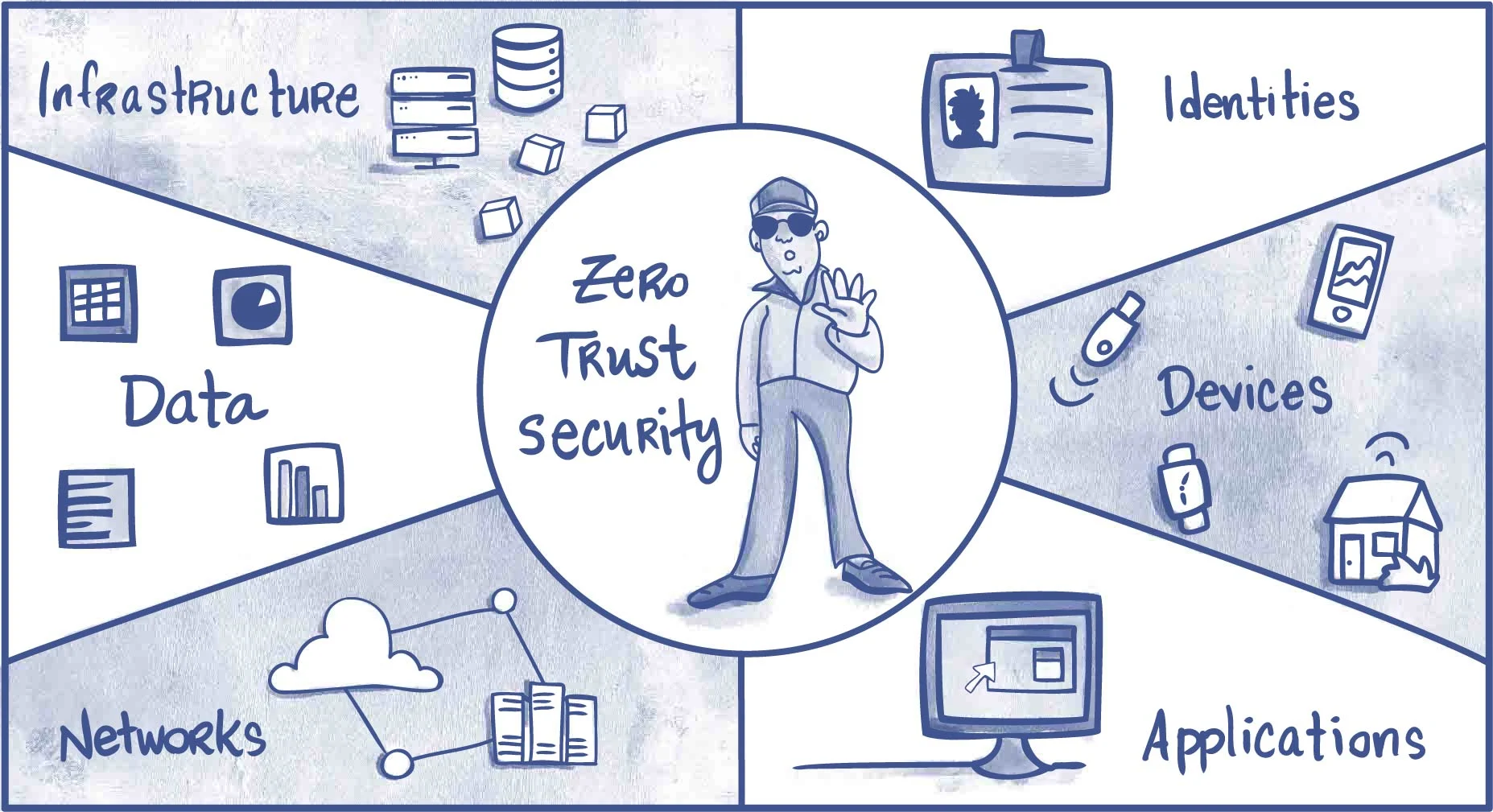
Despite being a buzzword, Zero Trust is a fundamental concept with concrete benefits and pillars. But how do you implement it? The right ZTNA solution can help. ZTNA products reduce the attack surface by enforcing identity and context-based access control. They can be deployed as a gateway in front of a protected resource or as an agent on the device.
Security
Zero trust solutions create an identity-based, logical access boundary between enterprise resources and external applications. This dramatically reduces an organization’s exposure to cyber threats, allowing them to protect data and networks without the limitations of traditional virtual private network (VPN) solutions. Choose zero trust network access providers offering comprehensive security measures to keep your organization safe. Look for a solution that uses multi-factor authentication, micro-segmentation, and continuous monitoring. It should also integrate with your existing systems and infrastructure, making implementation easier. The right zero trust solution should offer security services such as device posture assessments, which verify whether a user’s device meets specific requirements, such as operating system version and usage of anti-virus software and disk encryption. It should also provide unified endpoint management (UEM) integrations, allowing you to connect users directly to apps from the Internet without going through the corporate network. Also, choose a vendor that can identify your network’s suspicious behavior and abnormal behavior patterns. This can be accomplished through advanced analytics and telemetry that collects information from devices, communications, networks, and users to assess the security posture of your environment. This data is used to detect and respond to threats, providing continuous monitoring to stop breaches in progress. This feature can be essential for employees working remotely or in the field.
Scalability
In the business world, scalability refers to the ability of a company to expand and grow without compromising its structure or resources. This is a crucial characteristic in a zero-trust network access provider because it ensures that the solution can meet your business needs now and in the future. With a scalable zero-trust architecture, you can protect remote workers and limit their access to applications and data by verifying identities and devices in real time. This prevents lateral movement from breaches and decreases the “blast radius” of damage attackers can cause. It also reduces the need for expensive hardware and software VPN devices that can create latency and limit performance. Choose a zero-trust network access vendor that supports multiple devices and operating systems, integrates with your existing security frameworks and cloud infrastructure, and provides the functionality to assess user and device posture before granting secure access. The solution should support your organization’s use of MFA (multi-factor authentication) at every connection point. MFA includes a combination of checks that confirm a user’s identity, such as security questions, email verification, text messages, security tokens, and biometric ID checks. A scalable zero-trust architecture is essential because it helps protect users and data even in a breach. It can quickly scale up to handle bursts of traffic or heavy loads and then back down when demand is lower.
Integrations
The most effective Zero Trust solutions provide a comprehensive approach to security, enabling organizations to securely connect employees and customers across all their infrastructure, applications, devices, and locations. This requires strong authentication and authorization, device and user posture assessments, and identifying threats and abnormal behavior across the network. Choose a provider that can easily integrate with your existing systems and infrastructure. This will ensure that your Zero Trust solution works smoothly and seamlessly with your existing infrastructure and reduces the risk of disruption. Also, consider your organization’s growth in the future and look for a scalable provider that will allow you to grow your Zero Trust architecture quickly. A zero-trust network access provider should support your organization’s remote or hybrid work model, whether that’s through the cloud or on-premises. Additionally, it should support third-party users such as contractors, suppliers, and partners who represent a heightened security risk and are not managed by IT. Zero trust seamlessly connects these users to internal resources without exposing them to the corporate network and protects data from malicious activity. A Zero Trust Network Access solution verifies and authenticates users and their devices, providing secure access to business applications without needing a VPN. It eliminates the need for privileged access and prevents the lateral movement of breaches that can cause catastrophic damage within the organization. This helps organizations protect their most sensitive information, enabling them to deliver the digital experiences that users expect.
Pricing
When choosing a zero-trust network access provider, it’s essential to consider pricing measures. Ensure the vendor’s solution is priced competitively and can scale as your organization grows. Furthermore, verifying that the vendor’s pricing model is aligned with industry standards would be best. It’s also a good idea to ask the vendor about any additional fees that apply, such as support, implementation, integrations, and more. Many organizations are moving toward a zero-trust strategy to protect sensitive data and reduce the risk of a cyberattack. But, implementing a Zero Trust architecture is challenging for many companies, especially as they seek to replace legacy remote-access VPNs and other traditional security solutions. As such, organizations must choose a Zero Trust provider that can meet the demands of their technology environment and workforce.
Moreover, the right zero-trust provider should deliver high-performance connectivity and ensure their solution is scalable to support future growth. To achieve these goals, the solution should authenticate users and their devices at the point of entry, verify device trustworthiness, leverage adaptive access policies based on user risk, and provide a seamless remote experience for workers. Furthermore, the solution should be easy to manage and integrate with existing systems. For instance, a solution combining IAM and MFA will allow administrators to see a central view of all current and historical access requests in a single glass pane, making troubleshooting issues more accessible.


